Published research on cyber-attacks largely focuses on the security of data on in-life devices. Security budgets are typically assigned to maintain devices throughout in-life operations, leaving little to no provision for end-of-life cover. This gap in data security could have ramifications if left unchecked.
Decommissioned data-bearing devices sitting in employees’ cupboards, offices on site or a company warehouse, that have not been securely wiped and sanitized, may be gaining dust, but the residual data remains easily accessible.
Data security and the impact of cyber-attacks
In 2019 research, Blancco concluded that more than a third of businesses studied were taking “considerable risks” with data on end-of-life devices through insufficient sanitization, poorly audited chains of custody, and insecure storage. Blancco found that where the specific focus was placed on the physical destruction of these devices, it was often an unsuitable process. 80% of businesses’ had out-of-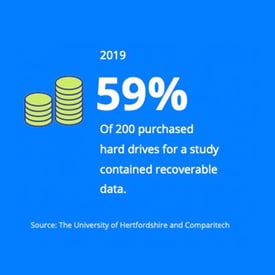 use equipment in storage, and the majority were conducting data erasure over a month after the device was decommissioned, enabling a window of opportunity for hackers.
use equipment in storage, and the majority were conducting data erasure over a month after the device was decommissioned, enabling a window of opportunity for hackers.
Additional research by Blancco estimated that roughly 42% of secondhand hard drives on eBay contain residual data.
The University of Hertfordshire and Comparitech found that 59% of 200 hard drives purchased online for their 2019 study contained recoverable data, including employer payment records, military documents, passport scans, and visa applications. They noted that since a previous study in 2008, the amount of recoverable data from secondhand drives had increased.
British Telecommunication’s research made the headlines when it revealed that a hard drive bought online to study data cleansing contained test launch procedures for the US Terminals High Altitude Area Defense (THAAD) ground-to-air missile system. Despite the potential severity that this case showed, the later studies still highlight the gap between decommissioning and data destruction.
The UK Government’s Cyber Security Breaches Survey 2021 found that businesses deploying security- or user- monitoring tools had actually decreased from the previous year. 35% of businesses used security-monitoring tools in 2020, which dropped by 3% for 2021, and 40% used usermonitoring tools, which dropped by 2%.
Obsolete devices pose an immeasurable risk as businesses are less likely now than the year prior to have a full understanding of what data is stored and processed on devices to be able to protect it sufficiently.
The COVID-19 pandemic saw an overnight need for remote working solutions with increased demand on cloud working from a workforce equipped with on-site data security policies. Despite this, Gov.uk reported that 84% of businesses said the importance placed on cyber security was not affected by COVID-19, implying that data protection policies were not updated to reflect the change to cloud services and instead, monitoring usage dropped.
Cyber-attacks pose a very real and acknowledged threat to businesses, even more so with a shift to remote and hybrid working where pre-existing security policies may not be stringent enough to cover an increase in cloud-based working. The research shows that data security investment largely focuses on devices in-life, and that end-of-life devices are not explicitly addressed.
The gap between in-life and end-of-life devices provides a significant data security risk with potentially severe financial and reputational implications for an organization.
Leaving a gap in your security
Your security is only as good as its weakest link. In enabling the gap we’ve addressed above, the business is exposed to several risks that stem from a heightened chance of cyber-attacks occurring. While the device and its data isn’t being monitored, it’s not being protected either. It may miss vital security updates or inclusion within your security policies. Such attacks may go undetected for longer periods of time. Foundry reported in their Security Priorities Study that 5.1 weeks was the longest average time to detect a security event.
The business would be open to:
- Loss of Personal Identification Information (PII). When suffering cyber-attacks, 46% of businesses profiled in the Global Intelligence Report: State of Cyber Security (2021, CSO) lost personally identifiable customer information.
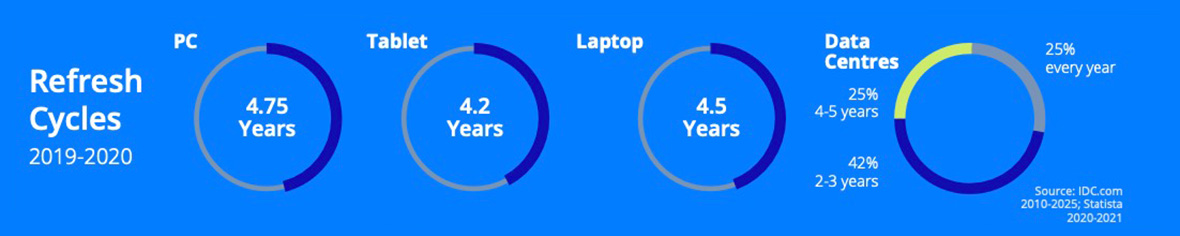
- Receiving fines for not complying to secure data storage and processing regulations. Applicable to not only theft of information online but also of the physical devices the data is stored on. 18% of cyber breach victims faced financial penalties, according to the CSO report. Typically, data-bearing devices follow the refresh cycles below; the older your device, the more likely it is to be a target for cyber-attacks as security updates and support decrease.
- Financial losses. Cyber-attacks could see finances directly or indirectly diverted from the business. There’s also the impact of loss of earnings caused by work delays while rectifying breaches. According to Statista, in 2021 23% lost £10,000-£49,000 due to cyber breaches and 18% lost £50,000-£99,000. The average cost of all cyber security breaches for businesses in the UK as of 2022 was £8040 for medium-large businesses and £861 for micro-small businesses.
- Damage to business reputation. The reliability and overall security of the company may be affected following a cyber-attack or data breach. Your lapse in security could also lead to a supplier or customer being breached. 33% of businesses suffering a cybersecurity incident experienced reputational damage (CSO).
Closing the gap
With lots of IT Asset Disposition (ITAD) provision available, you’re probably missing out on extra-mile service from getting value back to add to your future budget. The reason enterprises are placing more focus on the in-life security of data-bearing devices is very clear. However, the cause of the gap (the very little focus on the end-of-life part of the same device, as discussed in this piece) is not so clear and quite a concern.
It could be linked to:
- Lack of awareness – what a reputable ITAD partner can do for you is often something that enterprises are either unaware of or possibly not well informed about the extent of solutions available.
Data-bearing devices are often left in a room on-site, ageing, losing value and open to opportunistic theft. The disposition process is also incorrectly considered complex and laborious for the enterprise, which cannot be further from the truth. The need to keep IT and mobile devices within the 3-4 year age mark is important from a software version point of view which means they are as secure as possible. All of this creates a huge challenge for businesses and that is where IT Asset Disposition partners come in- securely de-risking this part of the devices’ lifecycle and taking away the entire challenge as well as providing a revenue share once complete. - Budgets – where to best spend money that will deliver peace of mind regarding data security and either fending off cyber-attacks or educating staff.
How does this link to your budget?
There is a lot of value in redundant IT and mobile devices, and the key is to extend their lifecycle once the data has been securely erased. This is achieved by uplifting their grade through refurbishment or repairing devices and making them ready to be redeployed or sold. This is an excellent way of enabling customers to be part of a circular economy whilst getting additional revenue back that bolster future budgets. Many ITAD providers do not offer the additional value uplift services, so it’s important to check before signing with a partner.